Protecting Your Nest With NIST Small Business Network Security Checklist
Founded in 1901, the National Institute of Standards and Technology (NIST) serves as America’s “standards laboratory.” A part of the U.S. Department of Commerce, NIST initially assembled standards and measurements for electricity, temperature, time and the like. Today, NIST provides technical leadership on a wide range of issues affecting the American economy. That includes setting the standards for small business information security.
“NIST is the de facto gold-plated standard for cyber security,” says Don Thompson, CEO of Capital Network Solutions in Sacramento. “If you can say that your business is NIST-compliant, then you’re in great shape.”
According to recent statistics, cybercriminals are increasingly targeting small businesses. Too many business owners discover too late that their business credentials are for sale on the dark web. Meanwhile, a recent spate of high-profile cyberattacks on hospitals and city governments underlines the dangers of malicious hackers and inattentive employees. However, whether because of low funds or less knowledge, small businesses tend to overlook necessary cyber security measures. Unfortunately, the effects of a data breach on a small business can be devastating:
- 43% of cyber attacks target small businesses.
- 14% of small businesses rate their cyber defenses as “highly effective.”
- 60% of small businesses shut down within six months of a cyber attack.
NIST bridged that knowledge gap earlier this year when they published Small Business Information Security: The Fundamentals. This 54-page document outlines NIST best practices regarding the fundamentals of cyber security. Moreover, it presents the information in non-technical language that is accessible to anyone.
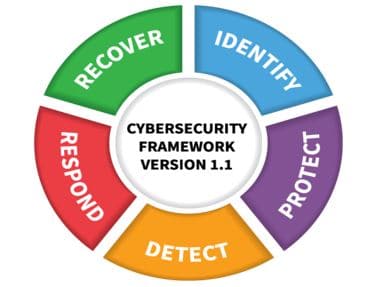
NIST recommends a five-pronged approach to cyber security:
- Identify
- Protect
- Detect
- Respond
- Recover
Understanding and Managing Risks
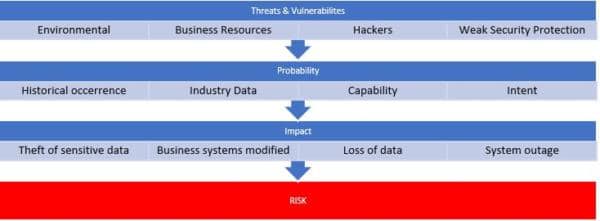
The first thing that every business needs to do is catalog their threats and vulnerabilities. By understanding your risks, you get a better idea of where to focus your cyber security efforts. Some of the most common risks include:
- Environmental (fire, flood, tornado, earthquake)
- Business Resources (equipment failure, supply chain disruption, inattentive and untrained employees)
- Hostile Actors (hackers, hacktivists, criminals, nation-state actors)
You should also identify what types of information your business stores, and document how that information gets used. While your small business may not store PII (personally identifiable information) on your customers, it probably does for your employees. Determine the value of your company’s data by developing an inventory of the data, and then inventory your IT hardware, software and applications.
Small Business Information Security: The Fundamentals will show how small businesses can provide essential security for their information, systems and networks. You can check out the entire document online, but we distilled it down to this NIST security checklist.
SMB CYBER SECURITY — NIST INFORMATION SECURITY CHECKLIST
IDENTIFY
PROTECT
DETECT

RESPOND
RECOVER
BEYOND THE NIST INFORMATION SECURITY CHECKLIST — ADDITIONAL TIPS FOR WORKING SAFELY AND SECURELY
- Pay attention to the people you work with and around.
- Be careful of email attachments and web links.
- Use separate personal and business computers, mobile device and accounts.
- Do not connect untrusted storage devices or hardware into your computers, devices or networks.
- Be careful about downloading software.
- Do not give out personal or business information.
- Watch for harmful pop-ups.
- Use strong passwords.
HOW CNS CAN HELP
At Capital Network Solutions, we possess over three decades of experience securing IT infrastructures for small businesses. We have the tools, the knowledge, the partnerships and the expertise to bring your business in line with NIST best practices for cyber security. If you are concerned the information security of your small business, call CNS at (916) 366-6566 to set up a free consultation.